When I was proposing this to customers, I observed that the limitations on securing /manageotp page is quite challenging for some use cases. What I'm about to explain here is, how not to allow users to register their own OTP authenticator but let admin to give control. It's a workaround I used and it's a manual method.
I'm not going to explain how to configure Citrix ADC for native OTP here (please follow https://www.carlstalhood.com/netscaler-gateway-12-native-one-time-passwords-otp/ ) for the deployment.
With my workaround users don't need to access /manageotp page at all. So restrict it for only admin's subnet on otp page login schema rule by setting it as follows; (if you want to access it for any reason)
http.req.cookie.value("NSC_TASS").eq("manageotp") && client.IP.SRC.IN_SUBNET(192.168.100.0/24)
or completely disable it.
If I explain the method in brief, its as follows; i will explain them in details later.
1. Citrix admin to manually generate a secret key for the user (we can use simple excel function for this)
2. Citrix admin to share the secret key to AD admin to configure the attribute of the users ldap profile
3. Citrix admin to share the secret key with the end user to manually enroll their mobile device (or admin can do it by himself on users device without sharing the key)
4. Citrix admin update his database (ex. excel) manually for future references
1. Citrix admin to manually generate a secret key for the user - this will help you to create a secret key for users (with MS excel)
1a. Open MS excel and paste "ABCDEFGHIJKLMNOPQRSTUVWXYZ234567" on a cell and name it as "Source"
1b. for a secret of 26 characters use following function to randomly generate a string.
=MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
& MID(Source,RANDBETWEEN(1,LEN(Source)),1)
it will randomly give you an out put similar to VLVLQJTETW2Z3O4UW5S4QQQCBT
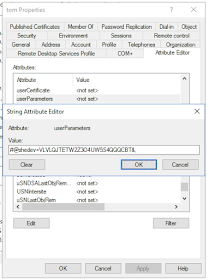
2. Citrix admin to share the secret key to AD admin to configure the attribute of the users ldap profile
2a. Citrix admin can share the generated secret with AD admin in following format (shedev is the device name we provide for the user)
#@shedev=VLVLQJTETW2Z3O4UW5S4QQQCBT&,
2b. AD admin can insert the given value to the selected attribute of the user ldap profile (in our case its userParameters)
3. Citrix admin to share the secret key with the end user to manually enroll their mobile device (or admin can do it by himself on users device without sharing the key)
3a. we can now share the generated secret key to the user
secret - VLVLQJTETW2Z3O4UW5S4QQQCBT
device name - shedev
3b. user or the admin by him self can configure the OTP Authenticator as follows; and save it
c. now you dont need to access /manageotp page and directly go to the gateway login page to enter dual factors
Notes;
1. make sure you you store secret keys in a secure place. I use a password protected excel to store them for the time being. something similar to following (they are some sample data set :) )
2. To automatically get the AD attribute value i use following function for E column of the above image
="#@"&D2&"="&C2&"&,"
3. To remove an OTP authenticator of a user, just clear the attribute value
=================================================
My next target is to write a small web page to get this task automated with maybe following functionality. if anyone smart enough to write it, let me also know. (unfortunately I'm not a web developer)
Add a user
1. Search a user from AD ldap
2. Generate a key for user (about 27 characters long random string)
3. Enter a device name
4. Store the key on a predefined attribute of AD ldap profile of the user
5. Store data to a local sql db (in a storefront environment we can use the same IIS and DB)
6. Send and email to the user with the key in it
Delete a user
1. Select user from the local db
2. Clear users attribute from the AD ldap profile
3. Delete user from the local db
Edit an existing user - (regenerate key)
1. Select a user from local db
2. Regenerate a new key
3. Clear existing attribute value and write new value on AD attribute of ldap profile of the user
4. Update local db
Share key with the user
1. Select a user from local db
2. A button to send an email to the user with the key in it
Good to have
1. A page to track changes done for users (all tasks listed above) - reporting
2. Encrypt local db
3. A login page to the site from an AD ldap user (admin user)
4. A page to list all the users in local db
Hope you enjoy my blog and helped someone. Any modifications or changes are always welcome :)




No comments:
Post a Comment